OverTheWire - Bandit Walkthrough (1 - 13)

OverTheWire hosts a collection of wargames that teach essential cybersecurity concepts through engaging and fun-filled challenges.
Bandit comprises exceptionally beginner-friendly challenges designed to teach you the fundamentals required for other wargames.
Here are the detailed solutions for the OverTheWire - Bandit levels. You are advised to first try the challenge on your own and then refer to these solutions
Level 0
This one is pretty easy. This teaches you how to connect to a host using SSH. You just need to connect to bandit.labs.overthewire.org with the username bandit0 and password bandit0 on port 2220.
ssh -p 2220 bandit0@bandit.labs.overthewire.org
Level 1
Here you need to get the password from the file in the current directory.
cat readme
This is the password for the next level. Copy the password and type exit in the shell to close the connection.
Level 2
Now connect to the same remote server with the username bandit0 and password obtained from the previous level.
ssh -p 2220 bandit1@bandit.labs.overthewire.org
For further levels, replace 1 in the username with the current level number.
The password is stored in the file called -. To open this, you can do the following:
cat ./-
Level 3
Here the password is stored in the file with spaces in the name. To open this file, you can do the following:
cat "spaces in this filename"
or
cat spaces\ in\ this\ filename
This one works because backslash allows us to escape special characters.
Level 4
At this level, we are given a directory named inhere and the password is stored in some hidden file. In Linux, the hidden file name starts with a period. To view them we can do ls -a which will display all files.
cd inhere
ls -a
cat .hidden
Level 5
At this level, the password is stored in one of the files in the directory inhere. The file is a human-readable. To look for the properties of all the files, you can do the following.
file ./*
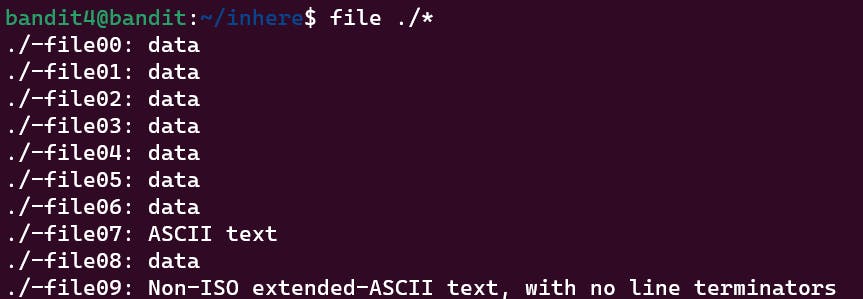
Here you can see that the file07 is an ASCII file. Opening it will give you the password.
cat ./-file07
Level 6
At this level, the password is stored in a file anywhere in the directory inhere. The file has the following properties:
human-readable
1033 bytes in size
not executable
So to search for a file with the following properties we can do the following:
find inhere -type f -size 1033c ! -executable
Here,
-type fwill only search for files-size 1033cwill filter all the files of size 1033 bytes! -executablewill filter all non-executable files
After running this, you are left with only one file.
cat ./maybehere07/.file2
Level 7
At this level, the password is stored in a file anywhere on the server. The file has the following properties:
owned by user bandit7
owned by group bandit6
33 bytes in size
So to search for a file with the following properties we can do the following:
find / -type f -user bandit7 -group bandit6 -size 33c
Here,
-user bandit7will filter all files owned by the user bandit7-group bandit6will filter all files owned by the group bandit6
Level 8
Here, we are given that the password is stored in the file data.txt next to the word millionth.
cat data.txt | grep "millionth"
Level 9
Here, we are given that the password is stored in the file data.txt and is the only line of text that occurs only once.
cat data.txt | sort | uniq -u
The sort will sort the lines in the file in ascending order and uniq -u iterates over them and searches for the line repeated once.
Level 10
The password is one of the few human-readable strings, preceded by several ‘=’ characters.
strings data.txt | grep "="
strings
Level 11
Here the password is encoded in base64. To decode do the following:
cat data.txt | base64 -d
Level 12
tr 'A-Za-z' 'N-ZA-Mn-za-m' <<< "str"
Level 13
Here, we are given a repeatedly compressed hexdump file.

We can see data2.bin in the header meaning it is a hexdump bin file. So we will reverse it. We can achieve this using xxd -r.
But first, as this will take a lot of decompression, we have to switch to a directory with the required permissions. We will create a new directory in /tmp/.
mkdir /tmp/hianshul
xxd -r data.txt > /tmp/hianshul/data
cd /tmp/hianshul
On doing file data we get to know that the file is a gzip compressed data. So, to decompress, we will change its extension and do the following:
mv data data.gz
gzip -d data.gz
After every step, we will get a file and we have to check its extension and decompress it accordingly.
BZIP2
mv data data.bz2
bzip2 -d data.bz2
GZIP
mv data data.gz
gzip -d data.gz
TAR
mv data data.tar
tar -xf data.tar
rm data.tar
TAR
mv data5.bin data.tar
tar -xf data.tar
rm data.tar
BZIP2
mv data6.bin data.bz2
bzip2 -d data.bz2
TAR
mv data data.tar
tar -xf data.tar
GZIP
rm data.tar
mv data8.bin data.gz
gzip -d data.gz
This is the final step. Here we will obtain an ASCII file with the password.
That's all for now. Stay tuned for more solutions.